Cześć! Zaraz omówimy ważne zagadnienie związane z szyframi blokowymi. Skupimy się na tym, co je charakteryzuje. Mam nadzieję, że ta wiedza przyda Ci się na egzaminie!
Czym jest szyfr blokowy?
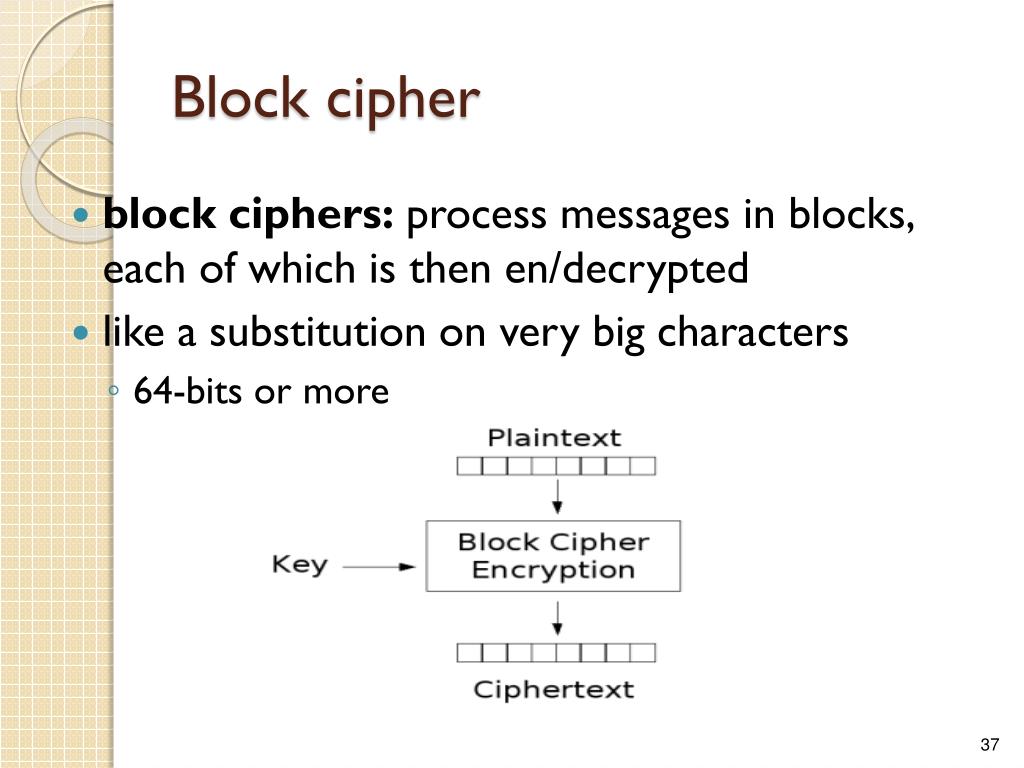
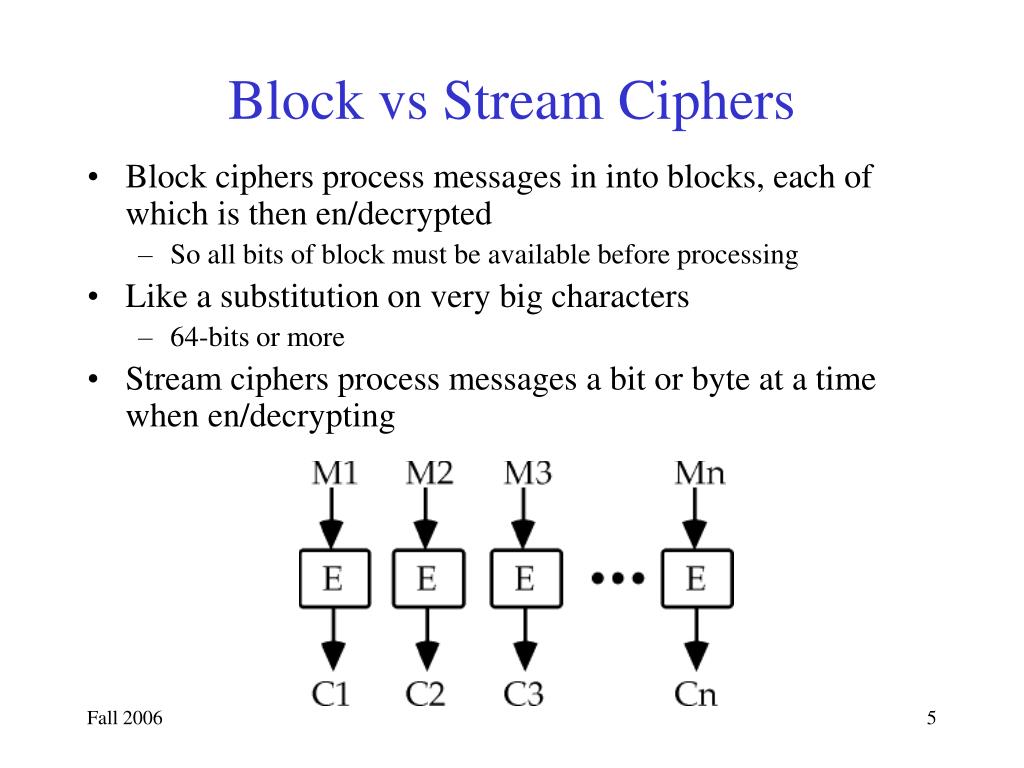
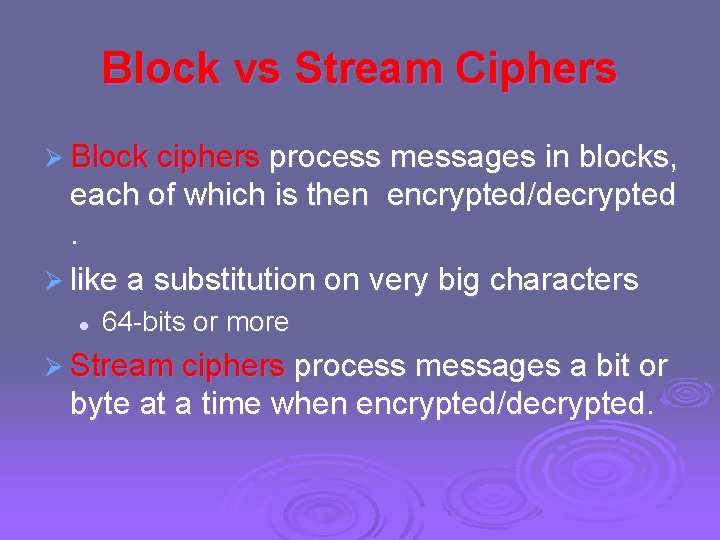
Szyfr blokowy to rodzaj algorytmu szyfrującego. Dzieli on dane na bloki o stałej długości. Następnie każdy blok jest szyfrowany oddzielnie. Długość bloku jest stała i z góry określona dla danego szyfru.
Weźmy przykład. Wyobraź sobie, że masz wiadomość. Szyfr blokowy dzieli ją na mniejsze kawałki – bloki. Każdy taki blok przechodzi przez skomplikowany proces transformacji. Wynikiem jest zaszyfrowany blok.
Kluczowe cechy szyfrów blokowych
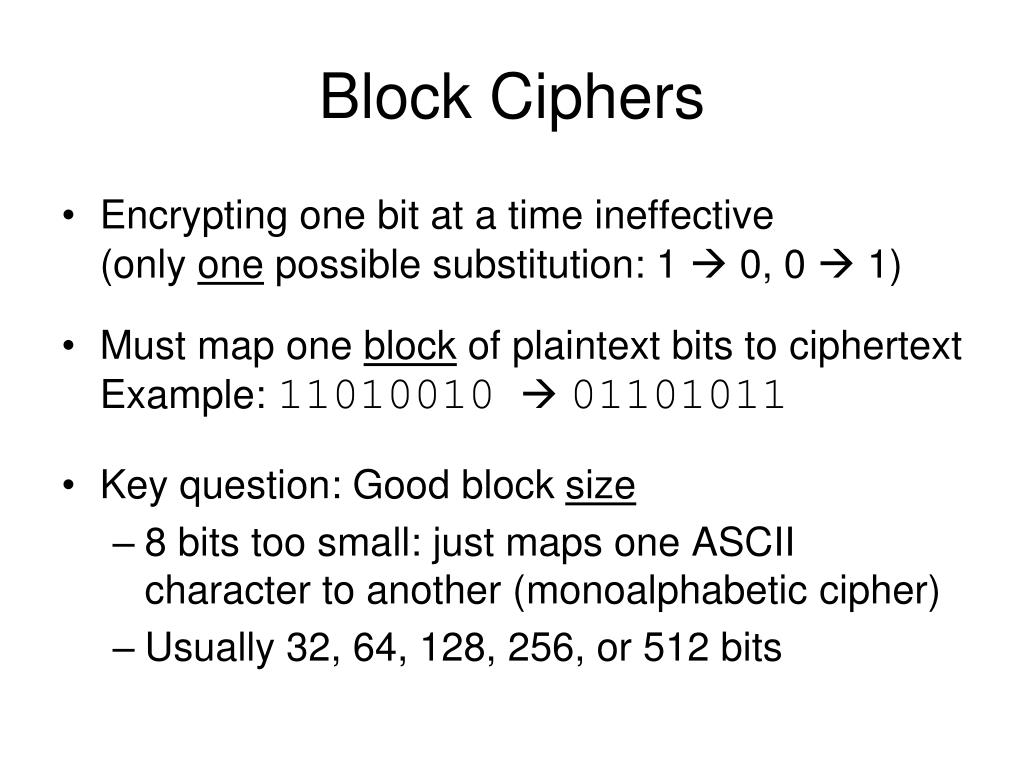
Jedną z najważniejszych cech jest **stała długość bloku**. Oznacza to, że niezależnie od długości wiadomości, szyfr zawsze dzieli ją na bloki o tej samej wielkości. Popularne długości bloków to 64 bity, 128 bitów i 256 bitów. Wybór odpowiedniej długości bloku wpływa na bezpieczeństwo szyfrowania.
Kolejną istotną cechą jest **użycie klucza**. Klucz jest tajnym parametrem, który kontroluje proces szyfrowania i deszyfrowania. Bez znajomości klucza, odszyfrowanie wiadomości jest bardzo trudne. Długość klucza ma bezpośredni wpływ na siłę szyfru.
Szyfry blokowe często wykorzystują różne **tryby pracy**. Tryb pracy określa, jak kolejne bloki są szyfrowane w relacji do siebie. Przykłady trybów to ECB (Electronic Codebook), CBC (Cipher Block Chaining), i CTR (Counter). Każdy tryb ma swoje zalety i wady, zwłaszcza pod względem bezpieczeństwa.
Przykłady szyfrów blokowych
Istnieje wiele popularnych algorytmów szyfrów blokowych. Do najczęściej używanych należą AES (Advanced Encryption Standard) i DES (Data Encryption Standard). AES, z różnymi długościami klucza (np. AES-128, AES-256), jest obecnie standardem. DES jest starszy i mniej bezpieczny ze względu na krótszą długość klucza.
Triple DES (3DES) to kolejna wariacja DES. Wykonuje szyfrowanie DES trzykrotnie. Ma to zwiększyć bezpieczeństwo w porównaniu do pojedynczego DES.
Podsumowanie
Zapamiętaj najważniejsze cechy szyfrów blokowych:
- Stała długość bloku: Dane dzielone są na bloki o stałej wielkości.
- Użycie klucza: Klucz kontroluje proces szyfrowania i deszyfrowania.
- Tryby pracy: Określają sposób szyfrowania kolejnych bloków.
Powodzenia na egzaminie! Mam nadzieję, że teraz lepiej rozumiesz szyfry blokowe. Pamiętaj, praktyka czyni mistrza, więc rozwiąż kilka zadań.





+of+chars+at+once..jpg)